SSH Client Auditing & Hardening
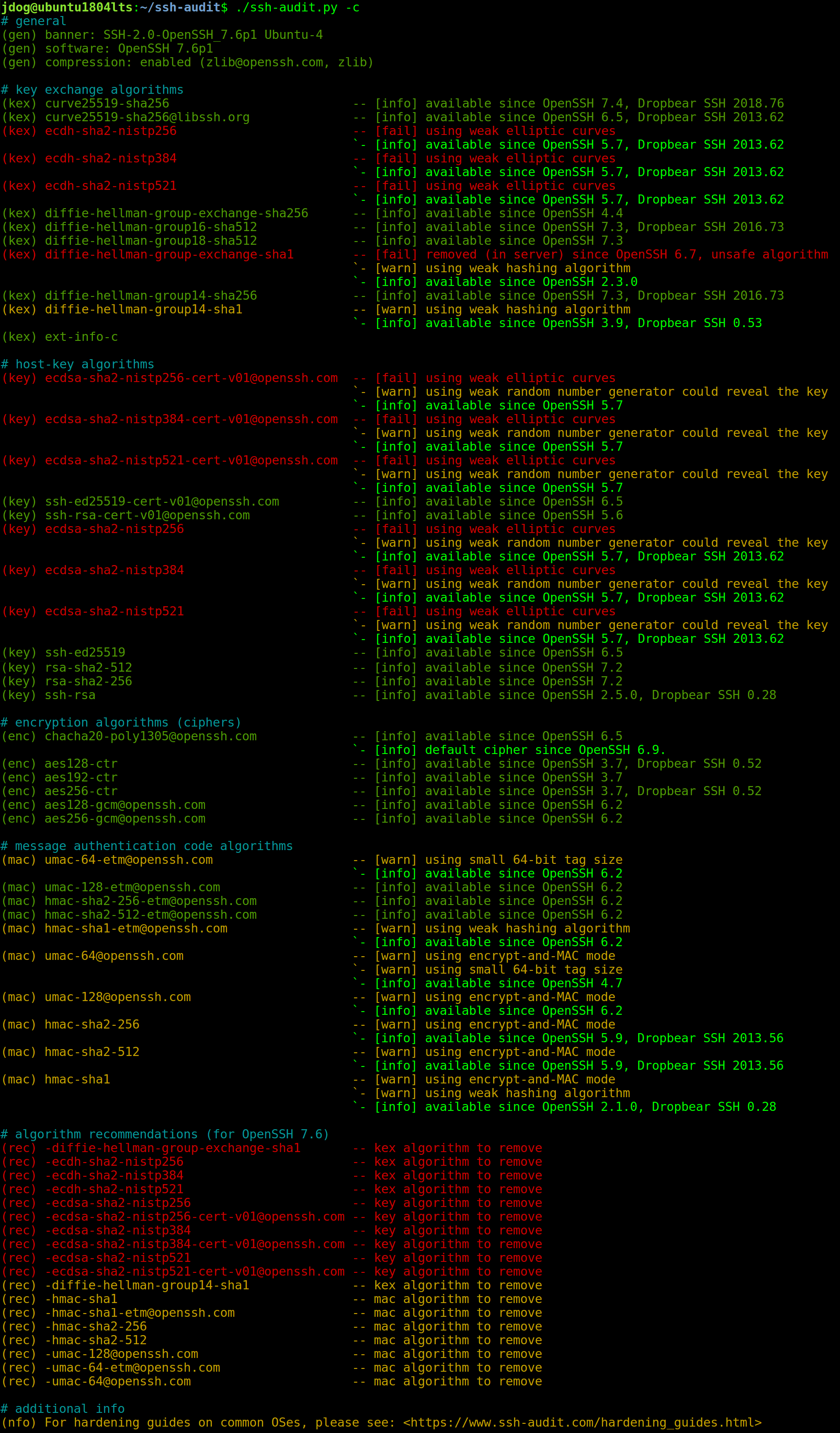
It’s been known for years now that SSH servers can (and should) be hardened by removing weak default algorithms. For example, recent versions of OpenSSH ship with algorithms suspected of being back-doored by the NSA (i.e.: ECDSA with the NIST P-curves), along with other algorithms with sub-128bit security levels.
But did you know that client software can be hardened too?
Why Harden Client Software?
In a world where all servers are properly hardened, there would be no need to re-configure client software. However, server hardening is unfortunately more rare than it should be, and you can only do it for machines you directly control. In that case, it’s very useful to upgrade your client’s defaults so you have assurance that only strong connections will be made.
There's Good News and Bad News...
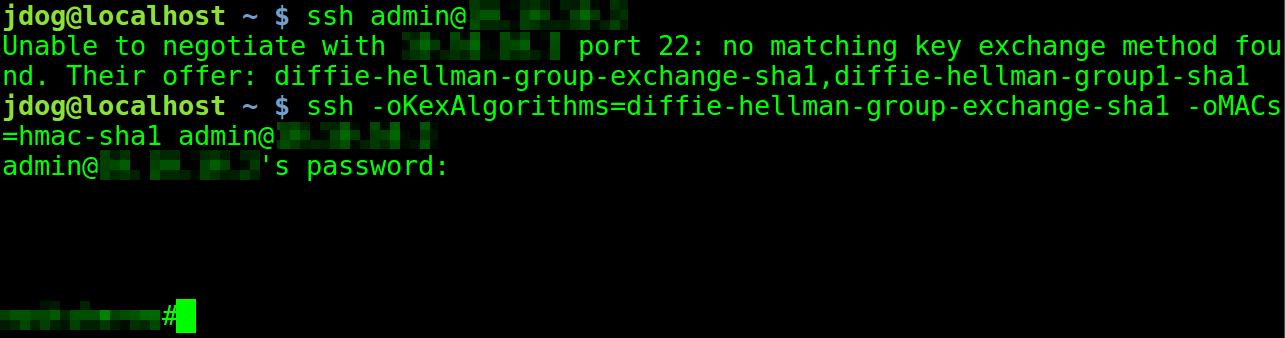
The good news is that the OpenSSH client can be easily hardened, either system-wide by putting configuration changes in /etc/ssh/ssh_config, or on a per-user basis in ~/.ssh/config. The configuration is done just the same as with the server component; all directives and algorithm names are the same, making this very easy to do. Afterwards, the OpenSSH client will terminate against servers that do not support strong settings. As a bonus, if one such server is encountered, the hardening can be overridden on the command line easily:
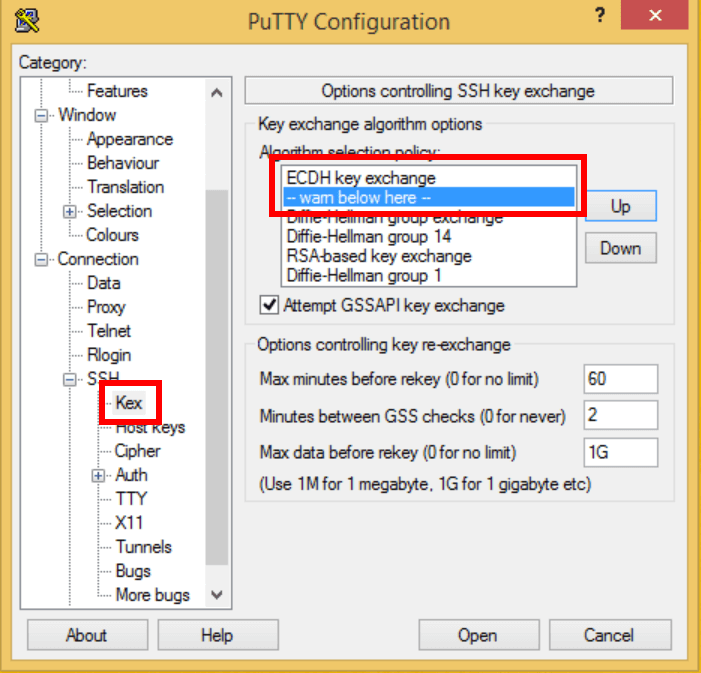
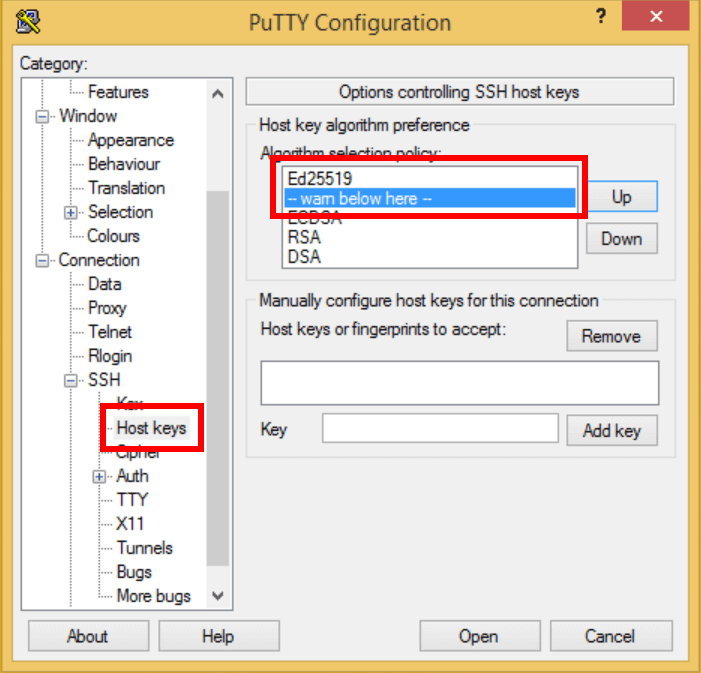
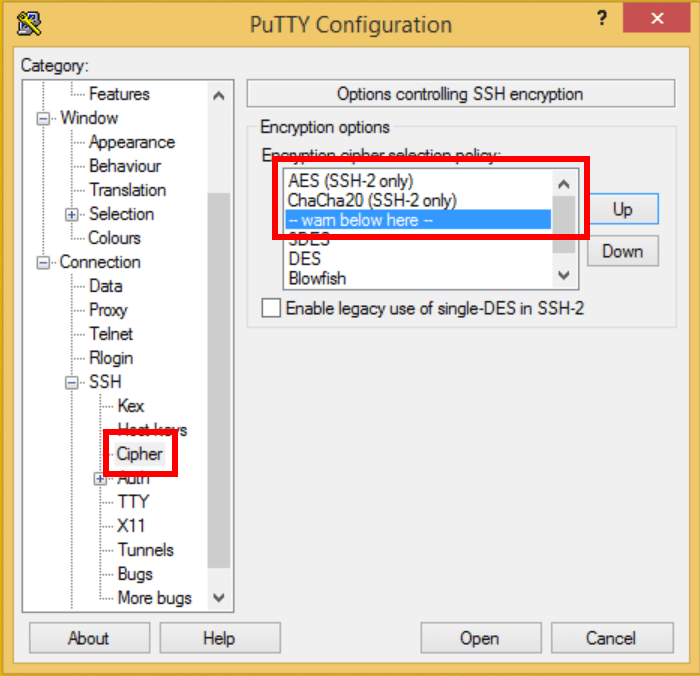
The bad news is that over in the Windows world, the PuTTY client cannot be hardened at the protocol level. It supports a very large subset of potential algorithms by default, meaning that if a connection is made to a very old router, it will succeed without even a warning that deprecated and weak options are in use (!). Changes can be made in the user interface, but they have no effect at the protocol-level; they will only trigger a warning instead of a hard-failure. And we all know what happens when you give users security options… (Hint: they almost always make the worst choices!)
There are currently two silver linings. One is that Microsoft recently ported OpenSSH to Windows 10 and Windows Server 2019. The second is that, with extra work, you can still configure PuTTY to issue warnings on weak connections. Here is a screen shot showing optimal settings (as of PuTTY v0.73):
Audit Example
With ssh-audit v2.1.0 that I just released a few weeks ago, you can use the -c option to cause it to listen on a local port for an incoming SSH connection. Once received, it will analyze the host key, key exchange, cipher, and MAC algorithms just as it would for a server connection.
Here’s a screen shot showing the result of a default OpenSSH v7.6 client (shipped with Ubuntu 18.04 LTS; weak algorithms are highlighted in red):
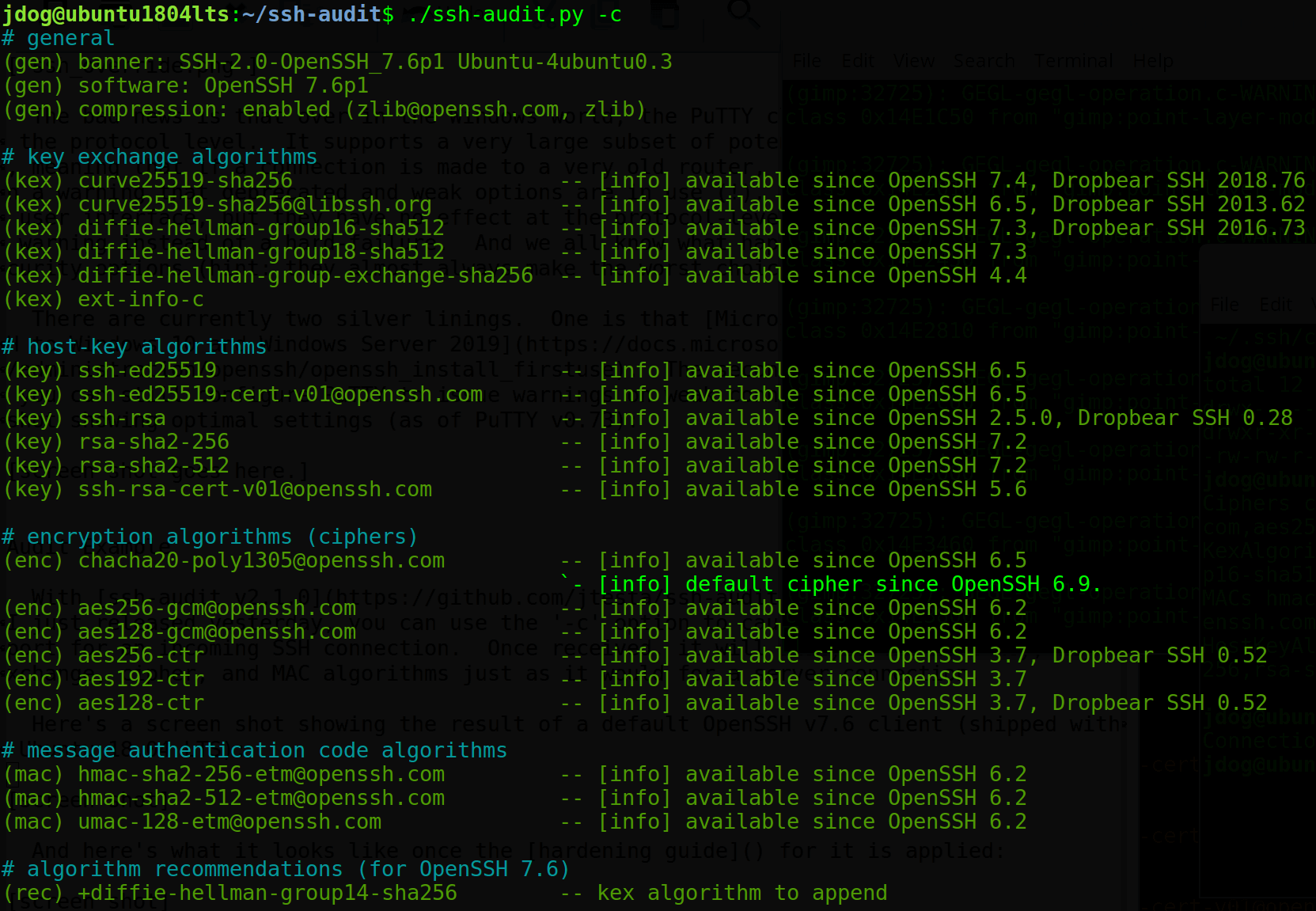
And here’s what it looks like once the hardening guide for it is applied:
Tools
The ssh-audit v2.1.0 command-line tool can be obtained from GitHub and used locally. It can also be retrieved from PyPI with: pip3 install ssh-audit
Additionally, I updated my ssh-audit.com web front-end so that testing can be done without installing anything locally.
Enjoy!
