Rainbow Crackalack Project Releases NTLM 9-Character Rainbow Tables!
Today, on behalf of the Rainbow Crackalack Project, I’m proud to announce the immediate availability of NTLM 9-character rainbow tables!
A Brief Recap
Ten months ago, in June 2019, I released the Rainbow Crackalack v1.0 software along with NTLM 8-character tables for free via Bittorrent. The tables could (and still can) be obtained by purchasing them on an SSD hard drive as well.
At the same time, I announced a Kickstarter project to raise at least $3,000 to purchase equipment to generate 9-character tables with. While the project failed to reach its funding goal, people from around the world nevertheless volunteered to generate tables for the project. I’ve been generating, collecting, and processing them in the last ten months, and now we’ve reached the original goal: tables that crack NTLM 9-character passwords at an efficiency of 50%!
Edit (Apr. 4, 2020): Based on some feedback I’ve gotten, I’ve realized that I should re-iterate here what’s mentioned on the main project website: modern rainbow table usage is NOT meant to replace rules-based cracking methods; rainbow tables only complement them. Rules-based attacks should be your #1 strategy. Only after that’s been exhausted should you consider using tables to extend your reach–and only for targeted high-value accounts, too.
There's Good News and Bad News...
Ok, so let’s get the bad news out of the way first: the NTLM 9-character tables are 6.7 terabytes large (!). Downloading them all via Bittorrent may take months.
The good news is that the tables can be purchased on a hard drive and shipped world-wide for only $250. Secondly, experimentation showed that only 938 GB of tables are needed to reach 10% efficiency, and 2.6 TB are needed for a 25% chance of cracking. Therefore, if a list of 30 domain administrator hashes were obtained from a Windows environment, even just a partial set of rainbow tables would still yield highly useful results in a penetration test. In other words, you don’t need all 6.7 TB in order to start using them.
Analysis of NTLM 9-Character Cracking
On a modest machine with one NVIDIA RTX 2070 GPU, reaching 50% effectiveness via brute force with hashcat is estimated to take 150 days. Using the NTLM 9-character tables, though, the same 50% mark would be reached in just a little over 2 days (51 hours, to be exact):
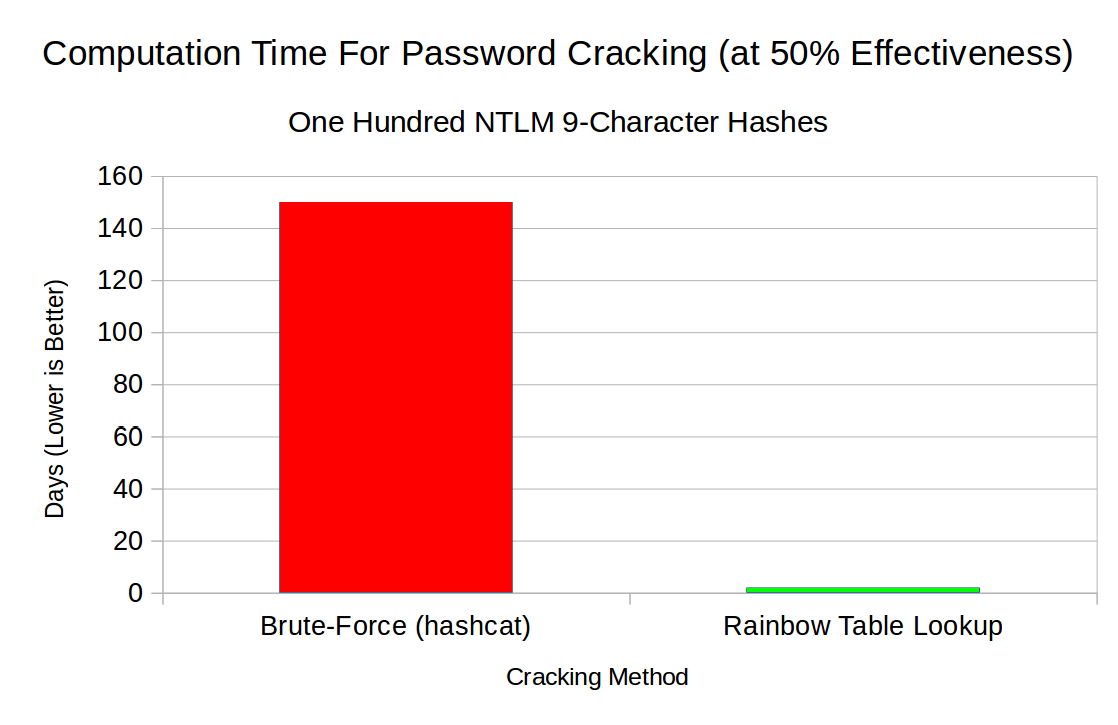
Note that, while one RTX 2070 GPU would be extremely under-powered for a modern cracking rig, the 75x speedup is roughly preserved as more GPUs and/or more powerful GPUs are added. In other words, using rainbow tables is always more effective than brute-forcing (once they’ve been obtained, that is…).
From a test run on 100 random 9-character passwords, it was found that 10% were cracked after processing 1,500 tables (938 GB). Furthermore, 25% of passwords were cracked after processing 3,700 tables (2.6 TB).
In real world conditions, observe that 100% effectiveness is not always needed. In many cases, only one password in a group of high-value accounts is needed. Hence, given a large enough set of hashes (i.e.: larger than 10), only 1,500 tables / 938 GB is usually needed for success.
Future Work
At this point, I’ve sunk $7,200 of my own personal cash into this project… not to mention hundreds of hours of labor! I plan on maintaining the code and keeping the tables available, but I don’t have any current plans to expand functionality or generate new tables.
If the community desires to continue, though, I’d be happy to coordinate efforts. Please let me know!
